Website Maintenance & Security – Who is responsible?
Are you looking into website security or website maintenance packages?
Website security is a large area of concern for many businesses, especially online stores.
It’s often not thought about until your website gets hacked or spammed. That’s usually when website owners start contacting hosting providers and web designers trying to find out who is responsible and how they can get their website fixed.
According to Forbes, around 30,000 websites are compromised each day. we are going to explore the different threats, who is responsible, how to stay protected, and what to do if your site still gets hacked.
What is website security?
Prevention is the best cure – Website security is ensuring that your website is protected to prevent harm from cyber criminals or spammers. There are many different types of websites such as plain HTML, Wix, and WordPress to name a few.
You don’t need to know the technical ins and outs of each website, you just need to make sure that yours is secure.
Most modern websites feature a content management system, a back end you can log into to make changes to your website’s content. The most popular choice around the globe is WordPress.
Each type of website will have its own set of best practices in keeping it secure. Whether you used a professional website designer or built your own website, website security is important.
Hacking your website could result in huge expenses for cleaning up the site. Furthermore, it could damage your reputation and discourage your visitors from returning to your website.
Website security is no single item. It is a broad term that covers many areas of a website, in particular methods of protection from known threats.
These methods could be SSL certificates, password cracking protection, bot protection, and securing contact forms just to name a few. We’ll take a closer look at each one further in the article.
Why are websites being attacked?
Hackers and scammers don’t care what size your business is. Whether you turn over twenty million per year or two thousand dollars in a hobby business the risks can be the same.
In fact, most attacked websites are chosen on a random basis. Or in other words, the hackers don’t plan which site they are going to hack.
There are, of course, cases in which hackers target the website of a specific brand or government. Such cases are often known as hacktivism. However, they are more an exception related to making a statement, rather than a common practice.
Hackers are most commonly running scripts on random websites looking for common vulnerabilities. The least challenging vulnerabilities are usually used to gain access to the website data.
Over 40% of all cyber-attacks are targeted against small businesses. – Symantec
Targeting small businesses shouldn’t come to a surprise as it is usually the owners of small business websites who leave security out of the main priorities list, whether it’s because of lack of time to do it themselves or due to lack of budget to hire someone else to do it.
As a result, around $600 billion is lost every year from cybercrimes.
Who is responsible for website security?
One things for sure it’s certainly not Paul Blart. Unfortunately, it’s rarely before a website gets hacked that the owner raises the question of who is responsible for the website security.
If you are running a good old HTML website, the responsibility falls mainly on the developers. If you are using a CMS (content management system) such as WordPress, Magento, Joomla, or Drupal, however, such a straightforward answer cannot be given.
Generally, the responsibility of the hosting company is to protect the server and not each particular website on it. A good example that explains the relationship simply is to look at the server as an apartment building and your website as an apartment in it.
While it is the management’s responsibility to take care of the building it is you who have to protect your own home.
In other words, in most cases, it’s the business or website owner’s responsibility to ensure their website is secure and up to date. That is unless you have an on-going website security/maintenance service. Many professional website designers are not security specialists.
“But I don’t know anything about securing a website?”
Well, before you start a website you don’t really have to know how to deal with website security. And once your website is up and running there are two options you can choose from.
The first option is to go down the self-learning route. There is no shortage of tutorials around the web that can guide you through the process. There are also plenty of applications and tools that will help you keep the process semi-automated.
Keep in mind, however, that maintaining your website’s security is an ongoing job that you will need to perform regularly.
The second option includes hiring a specialist to do it for you. And that’s where managed services come in. Just like mobile phone plans or health insurance, website maintenance services and packages vary from one provider to the next.
A reputable and trustworthy service provider should be able to help you with all details concerning website security, including but not limited to:
- Server repair and maintenance
- System upgrades
- Virus and malware removal
- Data backup and recovery
- Security auditing
Keep in mind that such services are rarely part of the hosting plans and need to be agreed on separately.
Most Common Website Threats
Many threats can compromise even the most basic of websites. If you believe you are safe because your website doesn’t use any complicated web applications, think again.
You probably still have some web applications integrated with your site, including:
- web analytics tools
- SEO applications and tools
- writing and grammar plugins
- social media plugins
- email integration
- contact forms
- chat applications
- third party plugins or extensions
- a template or theme
This is just a shortlist of potentially vulnerable applications reflecting on your website security.
To go into more detail, here are some of the most common threats to a website.
Brute Force Password Attacks
A brute force attack is one of the oldest methods hackers use to gain access to a website or server. A hacker will set up a computer that will try to guess the password used for your website.
They can guess anywhere between 30 passwords to 7 million combinations per second.
The main purpose of credential brute force attacks is to gain access to the admin area, control panel, or the SFTP server. If the attack is successful the hackers can execute different malicious operations ranging from spam campaigns to stealing credit card details.
To learn more, see Kaspersky’s article on Brute Force Attacks.
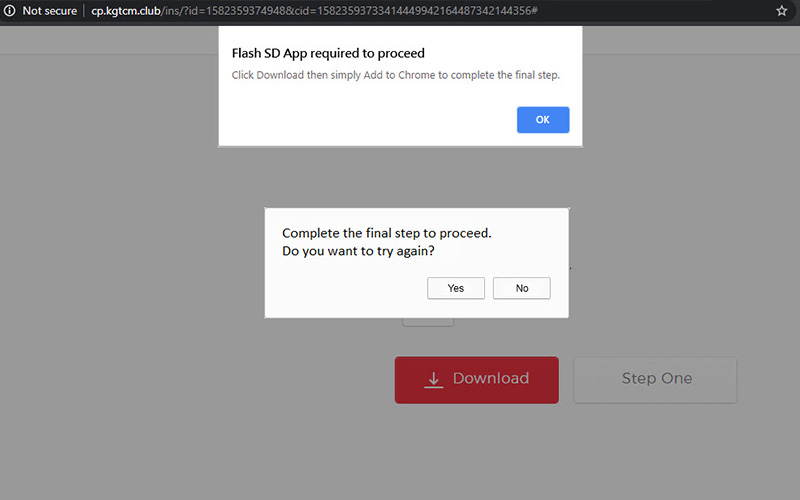
A common hacked WordPress website that redirects to a Malware website.
Stealing Website Traffic
Some attacks are targeted to redirecting your traffic from the search engines to the hacker’s money-making website.
They will usually imitate your site by using your logo and company colors to deceive the users who would think they are visiting your website and may even provide their personal details.
This form of malicious site or page resemblance is also known as defacement.
Cross-site Scripting
One of the methods to steal your traffic is cross-site scripting, also known as XSS. It allows the hacker to not only to high-jack the session and redirect your traffic but also to alter your website content.
XSS may also force the user’s browser to execute the hacker’s code when loading the page. If the user who loaded the code is logged in, the action will be performed using their assigned permissions level which could be critical if the user has admin permissions.
Distributing Malware
The term “malware” comes from malicious software.
When your website is used to distribute malware, the visitors will be prompted to download or execute a file that would then infect their PC with a virus.
Have you ever been prompted to update your flash player when visiting a website? This used to be one of the most common practices a few years ago. Of course, not all flash updates are malicious. But hackers learned to capitalise on this common user action.
Malware could also be used to steal sensitive customer data, distribute spam, and allow hackers to access your website. Sometimes hackers will also drop a backdoor to ensure continuous access to your website.
Stealing Resources
Mining cryptocurrency takes huge amounts of computing power. With the rise of the crypto trend hackers are also using malware to access the server’s or visitor’s configurations for mining.
This can slow down your website or even make it completely unusable by visitors.
SQL Injections
By using SQL injections, hackers may access and corrupt your database and then read, write, or delete your data. SQL injection attacks are performed by injecting malicious code into vulnerable SQL queries.
Stealing Personal Data
Some hackers take advantage of broken security configurations and authentication to high-jack active user sessions and steal the users’ personal data. This can also be accessed from a compromised database.
Blacklisting
Blacklisting is a way of flagging sites with malicious content to prevent visitors from downloading malware. It’s not a cyber attack in itself, but rather an unwelcome symptom of being targeted.
Blacklisting is done by search engines and antivirus companies who are frequently scanning for malware. If your website is infected and assessed to be posing a threat, it will be blacklisted and may be removed from search engine results.
When a user tries to access a blacklisted website a warning will also be displayed that will turn most visitors away.
Scaring away your visitors will hurt your website’s reputation and will increase your bounce rate. If you find your website to be blacklisted there are several steps you need to take to fix the issue.
- Locate and remove the malware as soon as possible. Every moment wasted affects your website’s ranking and reputation.
- Submit an official report to the search engine or antivirus company that has blacklisted you.
- Wait for the review from the respective company. If they find the issues to be resolved, your website will be whitelisted again.
- Prevent future blacklisting by increasing the security measures on your site. If you are not sure what to do you could subscribe to security services by hiring a professional to do the job for you.
Impact on the Users
Now you are familiar with the most common methods of attacking a website. But as a website owner, you are only one of the affected sides of the problem.
Having a clean and secure website is very important when you value your customers and want to build or maintain a good reputation. Protecting your website means protecting the users as well.
Here are some of the issues users may face after visiting an infected website:
- Stolen data – One of the main objectives of most cyber attacks is to steal sensitive customer data. While it may be something relatively innocent like an email that will later be spammed, it could also be critical data such as payment information.
- Phishing schemes – Phishing schemes are another way for hackers to try to obtain the user’s sensitive data. The idea is that the user is redirected to a seemingly safe or familiar page where they are prompt to enter the required data such as usernames, passwords, and credit card details. While this practice is mostly done through emails, it is not uncommon to appear though web pages directly. The hackers use a web page that is designed to look legitimate and so to trick the visitors.
- Malicious redirecting – This is a common practice where the user is redirected from the infected website to a malicious one that could be defaced or not.
- Session high-jacking – By high-jacking a session the user is forced to take unwanted actions on a website.
- SEO spam – SEO spam is another way to trick users into visiting malicious websites to drive traffic. This could be done by using comments or unusual links or pages.
- Stolen resources – Some malware even connects to the PC of the user to steal from its resources and use them for cryptocurrency mining or other nefarious purposes.
Website Protection
When it comes to protecting your website, it is important to note that there is no magic tool that will keep your data safe. Instead, you should rely on several features that add up to the highest possible level of security.
You protect a nation from invaders with an army, airforce, navy, and more. Just so, you need to protect your website on multiple fronts. Here are the most necessary measures you can take to protect your data.
SSL Certificates
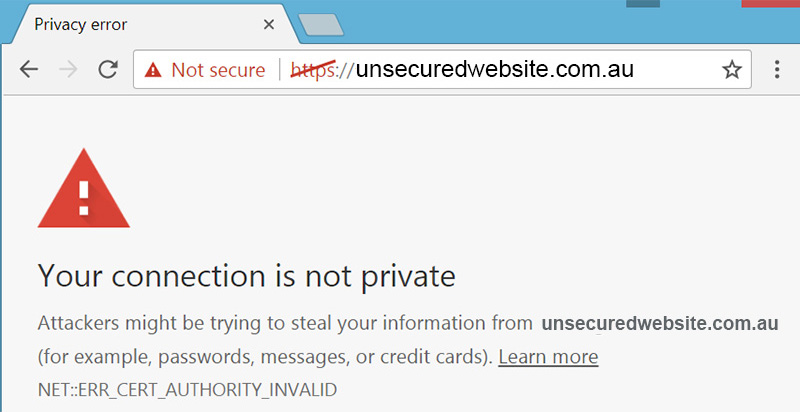
SSL (Secure Sockets Layer) certificates are now a must if you have a website that collects user data and if you are looking to rank high in Google.
SSL certificates are small data files registered to a domain and the respective organization details. When the certificates are configured and activated, they switch the protocol from “HTTP” to “HTTPS” which ensures a secure connection between your server and the browser of the user.
This secure connection will encrypt all information, especially sensitive data such as personal contact details, consumer credit card information, proprietary files, etc.
If you are running an eCommerce site, an SSL certificate will ensure that you meet PCI compliance, which will allow you to accept credit card payments as an online merchant. The requirements set by the PCI-DSS (Payment Card Industry Data Security Standards) aim to ensure that the cardholder’s details are properly protected.
Another reason why SSL certificates are an important feature of any website is that recently Google added the encryption to its ranking algorithm. This means that a website with a valid SSL certificate is very likely to outrank a competitor website using an HTTP protocol only.
Another feature from Google includes a message displayed to Chrome users when they are opening websites without a valid certificate. If the website has any form for submitting data, Chrome will warn the users that the website they are about to access is not secure.
Firewalls
Firewalls or WAF (Web Application Firewalls) are a common software solution to protect your system and data by monitoring and filtering the activity before it reaches the server.
Some of the methods used by firewalls include:
- Filtering – analyzing all data coming through the server against a predefined set of filters.
- Inspection – comparing the incoming data against a database of trusted information.
- Proxy – captures bad or unapproved traffic before it reaches the website.
Firewalls provide protection mainly against malicious bots that are automated to look for vulnerabilities on your website or cause DDoS attacks that may crash your website by sending overwhelming amounts of fraudulent traffic.
If you are using shared hosting it is very common to have no access to your firewall configuration, as the firewall is applied to the whole server.
Some hosting plans allow the website owners to upgrade to a dedicated firewall, which would give them control over their specific firewall configurations. For example, this could be used for better filtering out who can access your website and who cannot.
Sandbox Environments
A sandbox or dev environment will provide you with a secure way to test any new configurations, applications, or updates without the risk of damaging the current state of your website.
This will ensure that any possible vulnerabilities appearing from the applied changes won’t be directly available in your live environment. A sandbox environment will keep you both from ruining the user experience and avoiding hackers.
Data Backup
Data loss is one of the worst things that can happen to an active business. Even with careful management, accidents tend to happen.
Add to that the possibility for malicious attacks, and you’ll understand why this feature is so important to any serious business website.
Upgraded hosting plans usually provide data backup as a service. The backups can be automated or manual and when applied will restore a previous version of the website. In case the site is hacked, the backup can restore your website to a given point. For example, right before the breach.
Backups can also be used to avoid downtime in case of a server failure by calling extra server banks that carry a copy of the current version on a live server. Such hardware backups are known as redundant.
User Access and Password Management
Many websites allow different levels of access to multiple users. Whether they are members of your team, customers, or subscribers, they would need a user-specific password to access the content.
You would also want to assign specific permission levels for each role. For every specific role, these levels could vary from content posting to unrestricted admin-like access.
To achieve this in a secure way and protect both yours and their data, it is recommended that you use a trusted password management application.
If you wish to follow the best practices in the industry, you should also apply a password policy for all users depending on their assigned role. A predefined password policy will ensure that users with higher user access will have a more complex and strong password by meeting the set requirement and will restrict them from using basic or reusable passwords.
A password manager could also remove the option for manual password creation completely. Another major benefit of password managers is that they usually store the passwords in an encrypted vault and not in the cloud.
Two-factor Authentication
Two-factor authentication (or 2FA) means that the user has to go through an additional step to log in and ideally, only the real user would be able to pass the second level of authentication.
An example of a two-factor authentication process is when the user enters their login details, then receives a text message with a unique code, known also as OTP or one-time password. To access the content they have to provide the OTP within a given time frame.
Other details that may be required as a second step include, but are not limited to an email address, PIN code, or biometric data such as fingerprint for mobile devices.
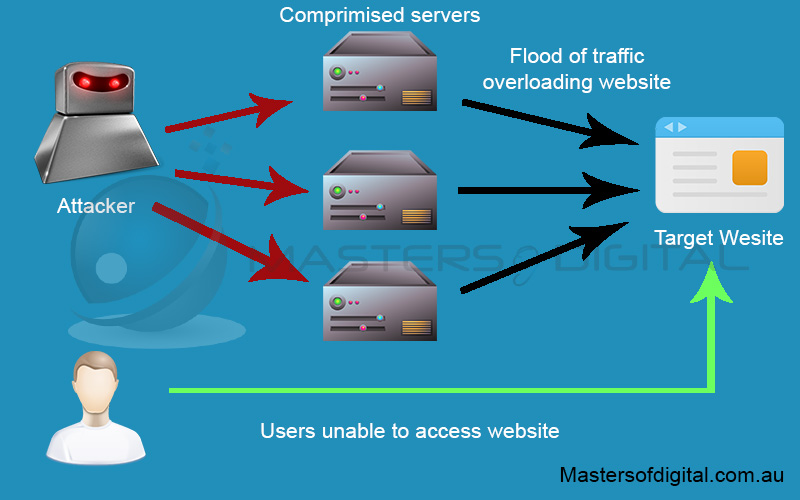
How a DDoS Attack stops users from loading your website.
DDoS Protection
DDoS stands for Distributed Denial of Service. One of the methods hackers use to attack websites is by sending overwhelming volumes of traffic to the website in a very limited time.
The overload can take a website with no or low protection completely offline, or at the very least prevent it from processing the actual incoming traffic.
DDoS protection monitors and filters the traffic coming to the website. When malicious traffic is captured, the protection rejects it while still allowing legitimate traffic to access the site.
The total number of DDoS attacks will double from 7.9 million in 2018 to 15.4 million by 2023. – 2018 data from Cisco.
Brute Force Detection
Not all hackers try to use the vulnerabilities on your websites. Some use a script that will attempt to gain access to the site by guessing the correct combination of username and password.
The script will automatically run as many as a million combinations per second.
Luckily, many hosting providers provide protection against brute force attacks by actively monitoring for multiple wrong submission attempts. And you can contribute to keeping your website protected against such attacks as well. Here are a couple of recommendations:
- establish a password policy to ensure your contributors use long and strong passwords
- install an application or a plugin that will limit the number of incorrect login attempts
- do not advise that the username is valid unless the whole username-password combination is correct
- automatically block attempts for login with invalid non-existing users such as admin, administrator, info, etc.
Virus Protection
Just like a regular home PC, a web server is running thanks to an operating system. And with this comes the most common threat of all, viruses and malware. While there could be some viruses that are relatively harmless, most are designed with malicious intent.
The good news is that most hosting providers turn to virus protection as a standard that needs to be met. Best case scenario, your hosting provider will monitor the servers closely and run regular antivirus scans.
Some upgraded plans provide the option to run manual scans on your website as well. In case your plan includes such a feature, be sure to discuss with your provider what needs to be done in case a threat is detected.
While the responsibility to clean the infected files usually falls to the owner of the website, some hosting providers may offer support plans to aid you in the process.
Website Scanners
A website scanner is an application or a plugin that automatically scans your website for vulnerabilities, malware, and other security issues.
The longer the infection resides on your website, the more it costs to clear it up. When scanners are run regularly, they help you locate and deal with the issues in a timely manner and reduce the losses.
When installing security-related applications or plugins, keep in mind that they need to access a huge part of your data, if not all of it. If you decide to install and run security applications on your website make sure you are using a proven and reputable solution.
Some scanners also tend to use a lot of your website’s resources which could eventually have a negative impact on your site’s performance.
Software Updates
If you’re running your website through a CMS system you most probably use a ton of third-party applications and plugins. After all, they make your daily work easier and your website prettier.
They are, however, among the most vulnerable points on your site and a point where most hackers exploit to get a foothold into your website.
It is very important to install all software updates for the plugins and applications you use as soon as they are released because these patches often include security updates and bug fixes that may turn out to be crucial in the attack prevention.
Regularly checking for plugin updates is a smart way to maintain the security of your website and increase protection from hackers.
Content Delivery Networks
The main purpose of CDNs or Content Delivery Networks is not specifically to serve website security. Content Delivery Networks allow a faster page load especially when users are trying to access an international website.
The traffic is also split across the CDN and so it doesn’t overload the main server. This function of the CDN adds an additional security layer against DDoS attacks.
Spammed vs Hacked Website
Spam is often confused with hacking or malware. But a spammed website is not a hacked website.
Spam is a term referring to unwanted emails sent from different companies to advertise products or services. Today spam is so popular that it accounts for about 60% of all emails.
Many websites are spammed through their contact form which does not mean that those who are sending the emails have gained access to the back end of your site.
Of course, spam can be used with fraudulent intent. Many spam emails contain links to malicious websites or executable files with malware that could eventually infect your site or PC.
Others may try to gain access to your website with the intent to steal your email list or turn the site itself into a spamming machine.
If your website is suspected to be used for spamming purposes, your domain and IP address may be flagged in spam databases. This would mean that the emails you sent to your subscribers will be automatically moved to the recipients’ spam folder. As you can imagine, this could make it very difficult to keep in contact with you customers.
WordPress Website Security
Today WordPress is the most widely used solution with over a 35% share of all websites around the globe and over 62% of the websites using a content management system.
Around 455 Million websites around the globe are built on WordPress. Even many well known Australian Businesses use WordPress such as Arnotts or Herald Sun.
One of the reasons why WordPress is such a popular choice is that it is free, open-source software that guarantees the users the freedom to run, share, and customize the software.
While the code is free for the end-users to view, however, it is also free for hackers and therefore it is a popular target for malicious attacks. Over 80% of all infected content management sites are run on WordPress.
Does that mean that WordPress is not secure? Of course not. Less than 10% of all WordPress hacks are a result of vulnerabilities in the platform core.
This means WordPress is no less secure than any of the other leading content management systems. It’s just more popular, which makes it a big target for malicious attempts.
Most of the successful attacks are coming through outdated installs, plugins, themes, and even users and hosting providers.
A proven way to start protecting your website from the get-go is to make sure your website is built using the best practices in the field to avoid as many potential weak spots as possible.
Three plugins were responsible for 25 percent of all WordPress hacks discovered in 2016 – Sucuri Report
Maintain a Secure Website
For many website owners, the idea of dealing with website maintenance and security sounds too complicated to even think about. Especially if you are running a small business or hobby website.
Reputable hosting providers and data centers go a long way to keep your website and your data safe from harm. Still, the main responsibility for keeping your and your customers’ data secure falls on you as the website owner.
To summarize it all, here are some basic steps you may want to follow that will greatly improve the security of your website on your end.
- Run a web application firewall – The firewall is the first line of defense for your website. Ensure your hosting provider offers one for the server, upgrade to a plan with a dedicated firewall, or install a separate application or plugin.
- Establish a password policy – The best way to protect your website from brute force attacks is to use long and strong passwords for all your users, regardless if they are contributors, clients, or subscribers. A good practice is to require the users to enter a password with 12 or more characters including letters, numbers, special characters, and caps. Some website applications and plugins may also have the option to prompt the users to change their password on a regular basis, for example, every 90 days.
- Assign permissions per role for your users – In case of a successful brute force attack, the severity of the damage will be greatly reduced if the user does not have full admin permissions. Some good rules of thumb when it comes to assigning permissions is to (1) always assign the minimum permissions required to get the job done, and (2) for temporary users grant access only for the time required to perform the tasks.
- Logout idle users – In the CMS you could change your settings to log out users who haven’t been active for a while, for example after 15 or 30 minutes.
- Always logout from the admin panel – While on the topic of logging out, don’t forget to log out of your admin area as soon as you’re done.
- Install an SSL certificate – Aside from encrypting your information, the SSL certificate will improve your Google ranking and inspire trust in your customers. The SSL certificate is a must if you are running an eCommerce website and want to be able to accept credit card payments.
- Keep your website up to date – Outdated software represents one of the greatest vulnerability points on your website. Hackers use these vulnerabilities to gain access to your website. Keep all your applications, plugins, shopping carts, and templates up to date by installing all available updates in a timely manner to reduce the potential for malicious attacks.
- Run manual backups – Whether your hosting plan includes automatic backups or not, it never hurts to run a manual backup as well. Especially if you’re a perfectionist who doesn’t trust others to go all the way. A regular backup will ensure that you always have a restore point to go back to in case of an accident or a hacker’s attack.
- Use domain privacy – Domain privacy hides your personal (whois) data for the website such as personal contact and location details. While this is not the greatest security protection, hiding as much data as possible from hackers adds another security layer to the complete website performance. Otherwise, the data may be used with malicious intent.
- Audit site for vulnerabilities – Don’t be afraid by the sound of it, vulnerability auditing doesn’t have to be done manually. There is no shortage of applications and plugins that will scan your website automatically. This is required to ensure that the custom configurations and tools are safe to use and do not present a potential threat. It should be noted, however, that no tool is 100% effective. With this in mind, if you are running a professional website, hiring a specialist to audit the site security is the best option.
- Install antivirus software – Although your website is located on a server, your home PC poses a potential threat as well. Malicious software like trojans and keyloggers may allow hackers to access your business data.
- Use CVV and AVS – If you are running an eCommerce website you need to ensure that you protect not only your personal details but your customers’ data as well. Including CVV (Credit Verification Value) and AVS (Address Verification System) at the checkout point will add another security layer in the protection against fraudulent attempts. By requesting this information the customer will have to have the code on the back of the credit card or the full address details in order to finalize the purchase.
- Create a security and maintenance schedule – Keeping your website secure is no one-time deal. If you have decided to maintain your website by yourself, keeping a strict schedule will help you keep your site up to date. While content and marketing may sometimes be overwhelming, a schedule will remind you to keep security among your top priorities.
In conclusion, it is important to remember why website security is so important and that it’s not something you do once and forget about it. The longer a threat remains unnoticed, the harder it will be to recover from it.
If you still think website maintenance and security is something too complicated and overwhelming, there is no reason to worry about your data. Hiring a specialist to do it for you will save you both time and potential headaches from running an outdated website.
Get In Touch For Your Website Maintenance
At Masters of Digital, our business is to grow your business. So feel free to contact us if you need reliable support in keeping your site and your customers safe.